New Malware: "Pro InvoiceWMZ45445"
During the last few days I received two mails with the following attachment:
Pro InvoiceWMZ45445.rar
which contains an .exe file with the same name:
Metadata of Pro InvoiceWMZ45445.exe:
- MD5:
4EE08155DB928C449EDEA28D6A68B8CA - SHA1:
6F57853E8788E2BD8E1433D8B2E1A701774593A4 - File Version:
1.0.0.1 - File Description:
TODO: <File description> - Created with:
Microsoft Visual C++ ver. 8.0 [DEBUG] / Visual Studio 2005
Indicators of Compromise (IOC) of Pro InvoiceWMZ45445.exe:
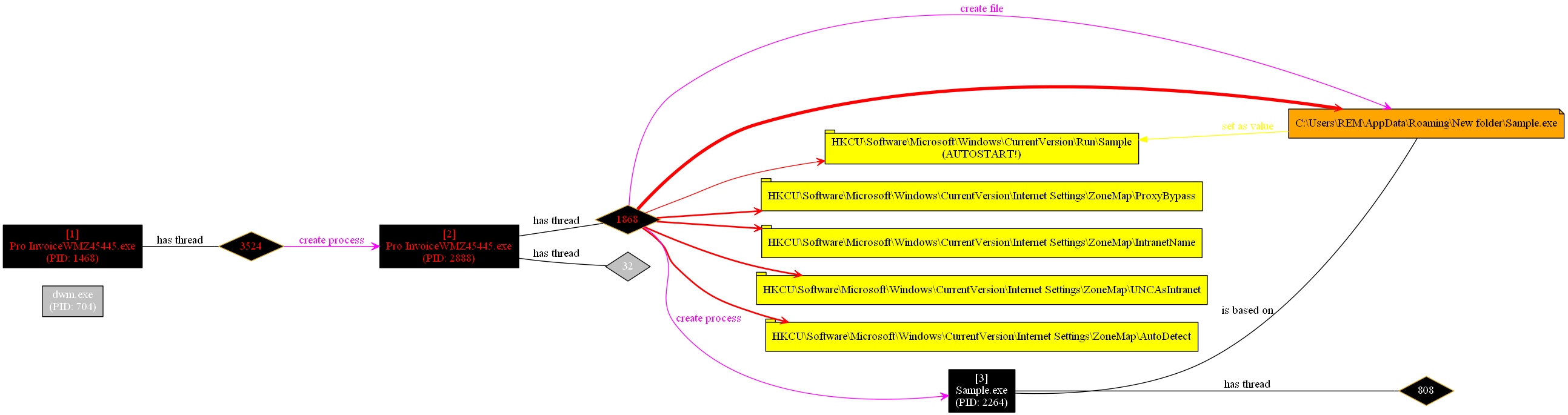
Upon execution, the file does the following:
- wait 30 seconds
- create a file
sample.exeunder%AppData%RoamingNew folder - starts the previously created file
- installs the
sample.exeunderHKCUSoftwareMicrosoftWindowsCurrentVersionRunSample (Autostart) - changes some Internet Explorer Setting
Metadata of sample.exe:
sample.exe has the same Hashes as Pro InvoiceWMZ45445.exe. Interesting, isn't it? So, this Malware isn't a Dropper; but instead it installs itself under a different name.
Indicators of Compromise (IOC) of sample.exe:
- creates the Mutant
Sessions1BaseNamedObjectsMUTEX-zZEeV-Zndko - tries to resolve fredamata81.ddns.net
- tries to connect to port 2015 of fredamata81.ddns.net (which seems to be closed at the moment)
- consumes a lot of CPU time (20% on my machine)
Additional Information
- The executable has Debug information stored externally in
d:bak_desktopnew folderstub1000_11_25_2015bdebugstub1000_11_25_2015b.pdb. I assume the file has been compiled on 2015/11/25. Maybe ;-)
More dynamic analysis will follow soon. First I must remove the call to IsDebuggerPresent(). But not today, anymore...
Update:
Virustotal has documented this specimen under https://www.virustotal.com/de/file/bf6c2c3f9cbb35023a38516e6b438f9125b7056429804c88c444fa37e0254956/analysis/
